[GitHub] [carbondata] BJangir opened a new pull request #3375: [CARBONDATA-3512]Index Server Enchantment
|
BJangir opened a new pull request #3375: [CARBONDATA-3512]Index Server Enchantment
URL: https://github.com/apache/carbondata/pull/3375 ### What changes are proposed 1. Remove the keytab dependency for IndexServer Currently IndexServer needs to configure keytab and prinicipal for both Client side and Server Side.But indexServer is super user and having super user's keytab and principal in client is not correct(specialy spark-submit). Since IndexServer is wrapped around spark application so no need to ask Keytab from User for IndexServer. 2. Authentication :- This happens in org.apache.hadoop.security.SaslRpcClient#createSaslClient .it checks getServerPrincipal(spark.carbon.indexserver.principal) and Server protocol (UGI of IndexServer). User need to configure spark.carbon.indexserver.principal properly. 3. Authorization(ACL):- Support User who can access the IndexServer. Authorization is controlled by hadoop.security.authorization. It is done in org.apache.hadoop.ipc.Server.Connection#authorizeConnection IndexServer has below senarios 1. Spark-submit,spark-shell,spark-sql :-> These type of spark Application has UGI where LoginUser and LoginUser will be same either based on kinit or based on spark.yarn.principal. Autorization is done in org.apache.hadoop.ipc.Server#authorize using IndexServer ProtocolClass and it's ACL list which is controlled by org.apache.hadoop.security.authorize.PolicyProvider(generally hadoop-policy.xml with key security.indexserver.protocol.acl by default *). 2. Spark JDBCServer :- It has UGI based on ProxyUser like user1(auth:PROXY)via spark/<DOMAIN>/<REALM>. where user1 is currentUser and spark is LoginUser (JDBCServer started UGI). This Authorization happens in org.apache.hadoop.security.authorize.ProxyUsers#authorize with proxyUserAcl list prepared by hadoop.proxyuser.<INDEXSERVER_UGI>.users ,hadoop.proxyuser.<INDEXSERVER_UGI>.hosts ,hadoop.proxyuser.<INDEXSERVER_UGI>.groups. check IndexServer document for detail about configuration. 4. TokenRenewer:- IndexServer is NOT Token based Hadoop Service. It does not required Delegation Token as IndexServer does not connect to KDC since it is inside SparkApplication(both, Indexclient and IndexServer) so take advantage of it. 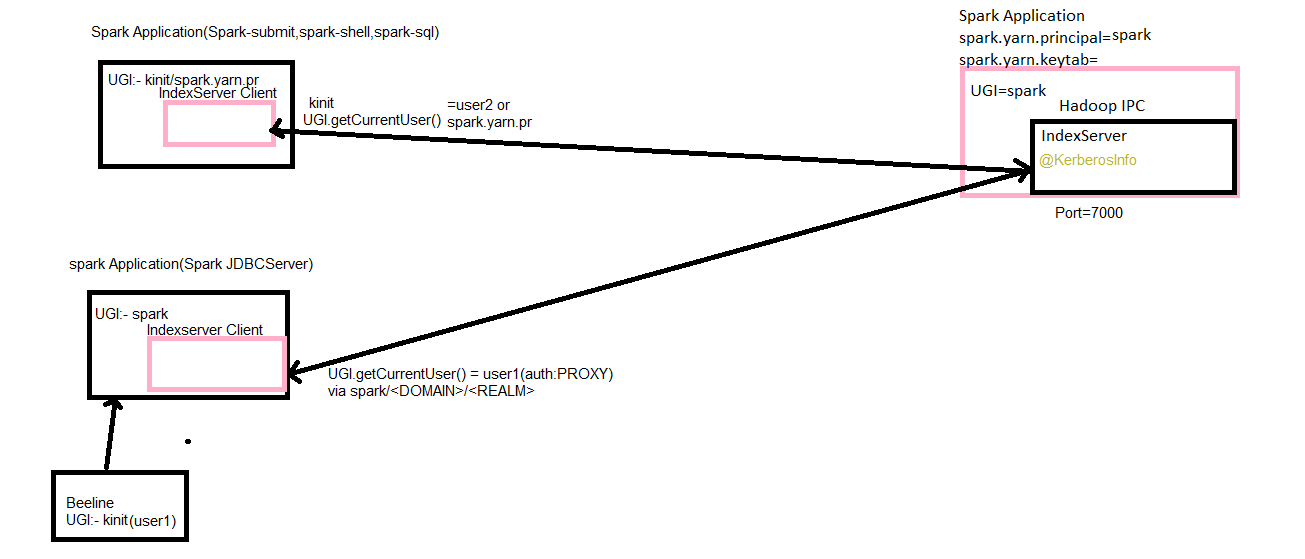 Be sure to do all of the following checklist to help us incorporate your contribution quickly and easily: - [ ] Any interfaces changed? - [ ] Any backward compatibility impacted? - [ ] Document update required? - [ ] Testing done Please provide details on - Whether new unit test cases have been added or why no new tests are required? - How it is tested? Please attach test report. - Is it a performance related change? Please attach the performance test report. - Any additional information to help reviewers in testing this change. - [ ] For large changes, please consider breaking it into sub-tasks under an umbrella JIRA. ---------------------------------------------------------------- This is an automated message from the Apache Git Service. To respond to the message, please log on to GitHub and use the URL above to go to the specific comment. For queries about this service, please contact Infrastructure at: [hidden email] With regards, Apache Git Services |
«
Return to Apache CarbonData JIRA issues
|
1 view|%1 views
| Free forum by Nabble | Edit this page |

